Generative AI Network Threat Detection.
Autonomous Response.
GenAI powered NDR platform that slashes operating costs by 50% while detecting threats 10x faster than legacy solutions.
Deploy agentless network sensors and let the AI SOC handle detection, analysis, and response. Focus your team on what matters.
The Evolution of AI and Network Threat Detection
Static IDS Rules
Signature-based with
classical ML
GenAI Powered NDR

Static Rules Fail
Traditional tools rely on static rules and signatures that can't keep pace with modern threats. Polymorphic malware and advanced threats constantly mutate to evade signature-based detection, rendering static rule sets obsolete.
Threat Actors are Evolving
The threat landscape is evolving faster than human response teams can adapt. New attack vectors and techniques are constantly being developed to evade traditional detection methods. Each year +20% new CVEs are discovered.
GenAI Native Defense
Organizations need AI-native, autonomous solutions that operate at machine speed. GenAI powered NDR platforms are the only way to keep up with the evolving threat landscape.
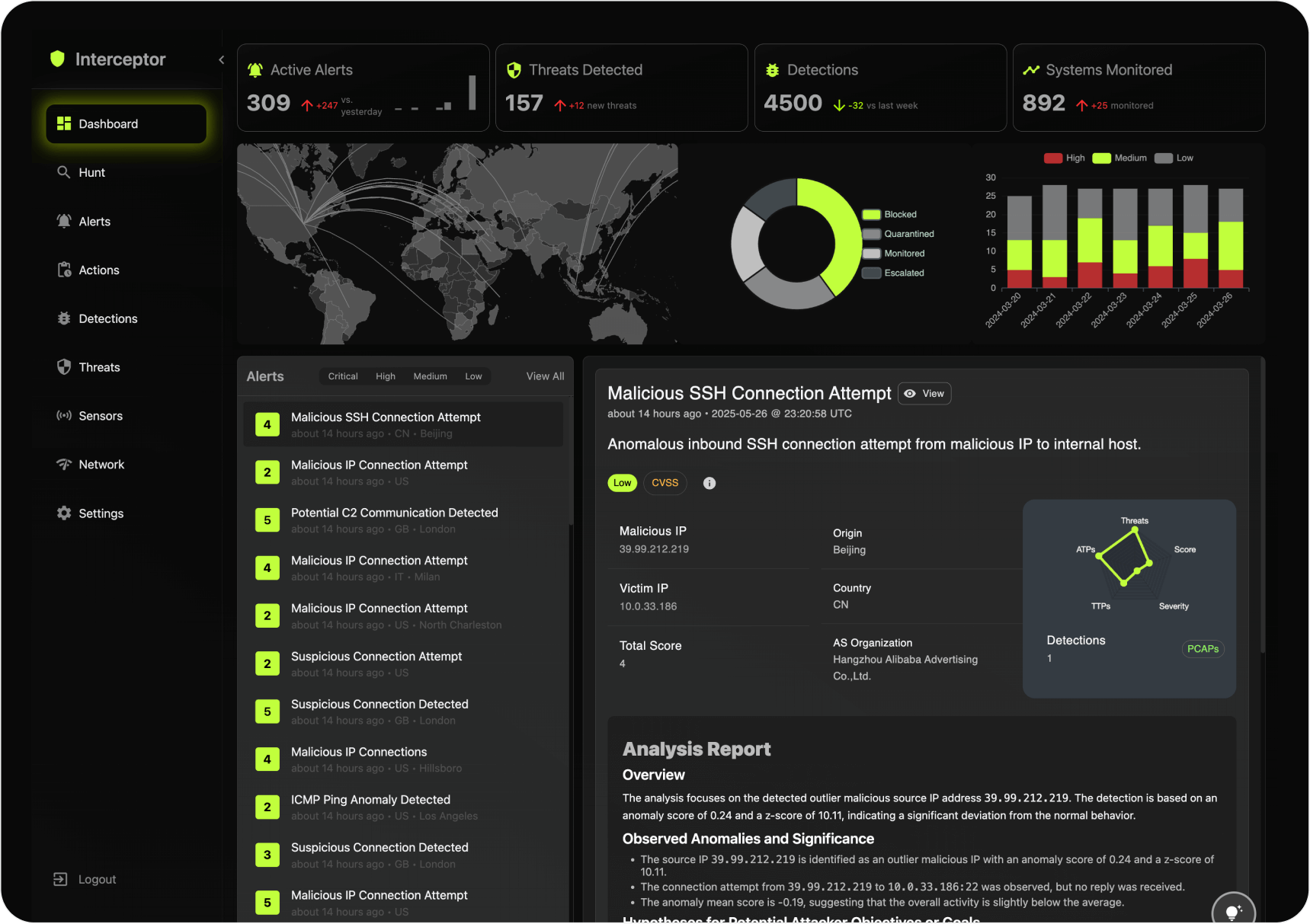
Interceptor NDR
The Future of Autonomous Network Defense
Next-generation network detection and response powered by generative AI
GenAI Threat Detection
Detects lateral movement and zero-day threats with generative AI-powered detection that adapts to new attack patterns.
Wire-Speed DPI
Deep visibility across all environments with wire-speed deep packet inspection at 1G–100G throughput.
Zero Disruption Deploy
Agent-less, cloud-native/virtual, easy on-prem install. Deploys in minutes with no infrastructure changes.
Unified Network Visibility and Autonomous Remediation
Interceptor combines full-spectrum visibility with machine-speed response, powered by deep learning and smart threat prioritization — delivering autonomous protection and total awareness through one unified NDR platform.
Deployment Flexibility
Cloud, on-prem, hybrid, and air-gapped environments
Integration Ecosystem
SIEM, SOAR, EDR, NGFW, and Cloud APIs
Dashboard Visualization
Unified, single-pane-of-glass control
Autonomous Mitigation
Instant AI-driven response to threats
A Critical Layer Beyond EDR & SIEM
Interceptor NDR fills the visibility gap that EDR and SIEM solutions miss, providing complete network coverage

Attack Surface Protection
Detects sophisticated adversarial techniques including zero-day exploits, Living-off-the-Land (LotL) binaries, and advanced lateral movement patterns that evade signature-based detection. By analyzing network protocols at the packet level, we identify anomalous SMB sessions, suspicious RDP tunneling, and covert channels that traditional security controls miss.
Unmanaged Device Defense
Adds visibility for unmanaged devices including IoT, OT, and shadow IT infrastructure. Estimates show that on average over 40% of devices are shadow IT which provides a significant blind spot for traditional security tools. This can further increase with BYOD and remote work.
Full-Spectrum Visibility
Exposes the attack vectors your security stack can't see. Captures east-west traffic, encrypted channel anomalies, and C2 beaconing patterns in real-time. Native SIEM/SOAR integration means threat indicators flow directly into your security orchestration pipeline—turning network telemetry into actionable intelligence without manual correlation.
Why Choose Cyber Ninja?
From Reactive Detection to Autonomous Cyber Defense
| Legacy NDR | Interceptor NDR | |
|---|---|---|
| Threat Detection | Limited pattern matching | GenAI-powered reasoning |
| Response Mode | Manual intervention required | Autonomous response |
| Learning Capability | Static rules and signatures | Self-learning AI models |
| Zero-Day Protection | Reactive, signature-dependent | Proactive behavioral analysis |
| Operating Cost | High manual labor costs | 50% cost reduction |

Take the Next Step
Experience autonomous network defense powered by GenAI. Deploy agentless sensors, slash operating costs by 50%, and detect threats 10x faster than legacy solutions.