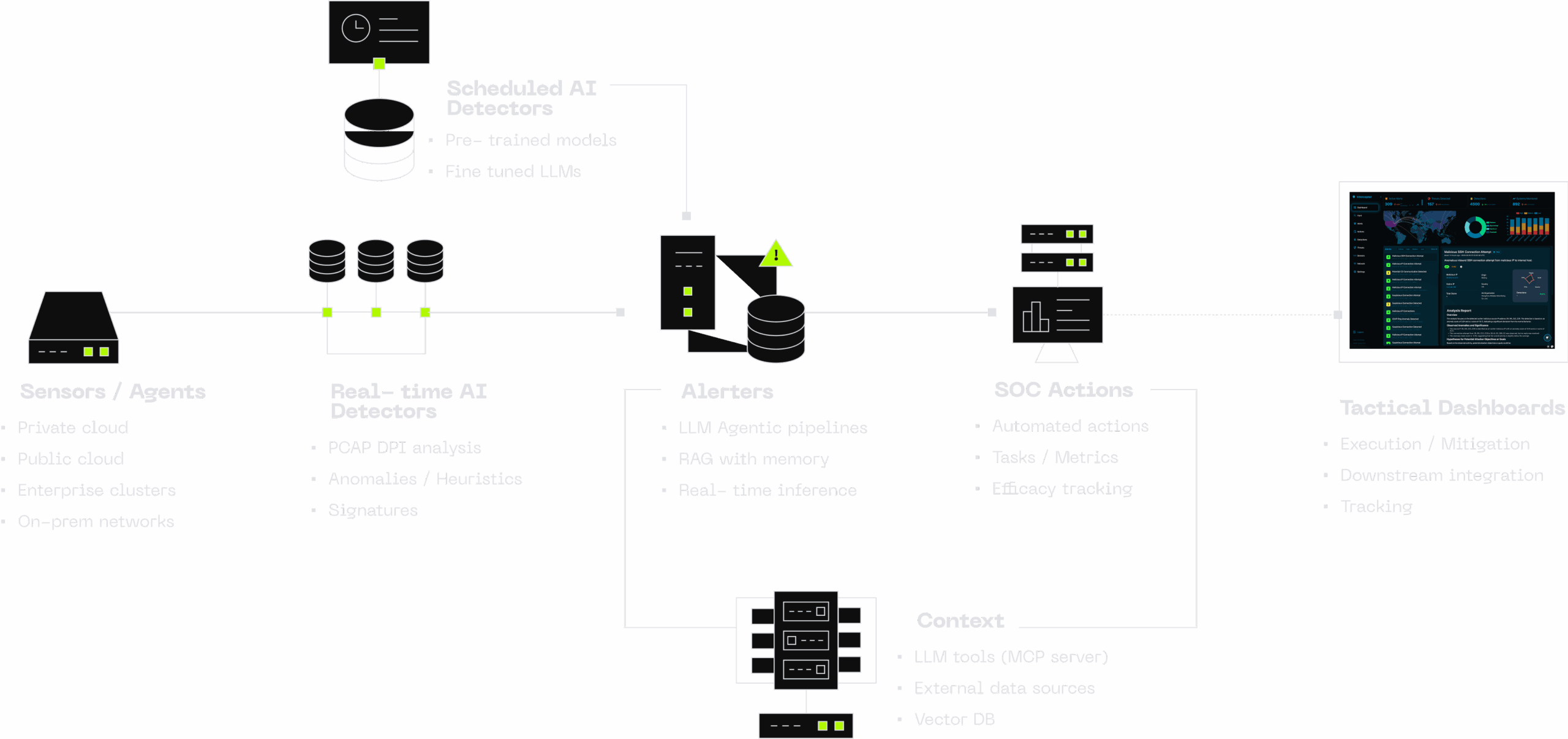
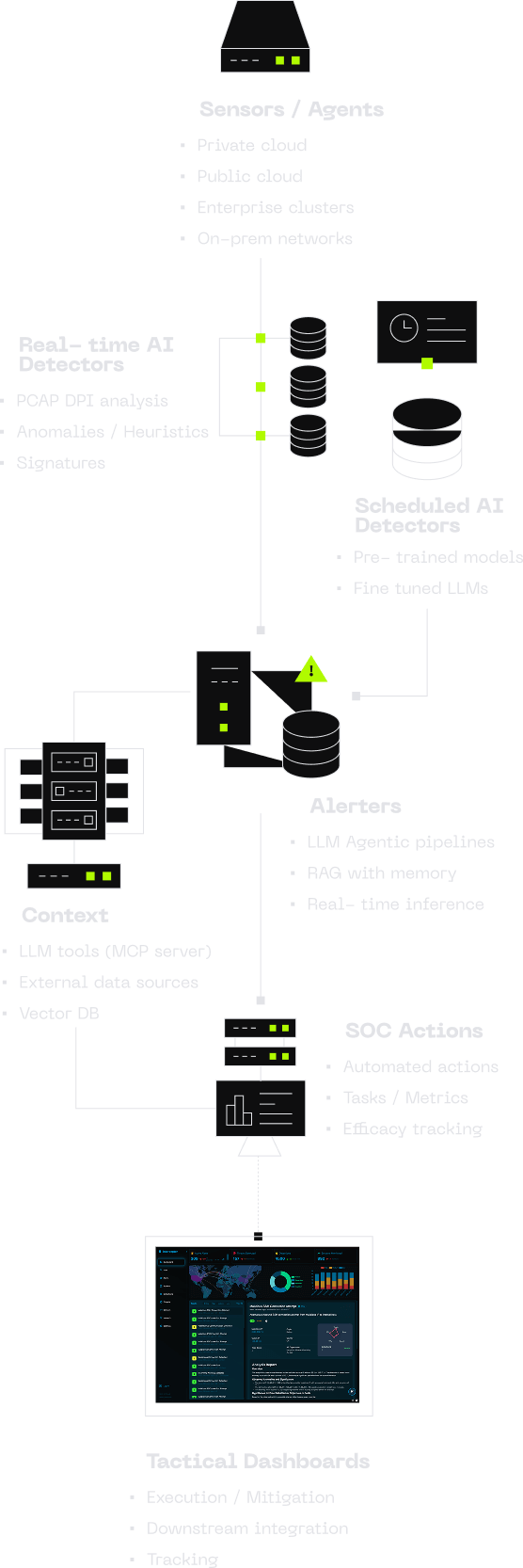
Generative AI-Powered Network Detection Framework
Built on cutting-edge GenAI technology to deliver autonomous threat detection and response at machine speed

GenAI Foundation Models
Pre-trained transformer models specifically designed for network data analysis
Transformer Architecture
Our foundation models utilize multi-headed transformer architectures with temporal attention mechanisms. Trained on petabytes of labeled network telemetry including full packet captures, NetFlow/IPFIX records, and MITRE ATT&CK-mapped attack sequences.
Edge Optimization
The models employ bidirectional encoding with positional embeddings to capture both spatial and temporal dependencies in L2-L7 traffic patterns, achieving sub-millisecond inference latency through quantization and model distillation techniques optimized for edge deployment.
Continuous Learning
We implement federated learning with differential privacy guarantees for continuous model adaptation while preserving customer data sovereignty. Our online learning pipeline incorporates adversarial training against GAN-generated attack variants and maintains separate specialist models for protocol-specific analysis.
Cognitive Detection Framework
What sets us apart from competitors: True cognitive reasoning for threat detection
Traditional Approach
- ✗ Static rule-based detection
- ✗ Signature matching only
- ✗ High false positive rates
- ✗ Manual analysis required
Cyber Ninja Approach
- ✓ Cognitive reasoning with GenAI
- ✓ Behavioral pattern analysis
- ✓ Context-aware detection
- ✓ Autonomous investigation
Our cognitive framework uses pre-trained foundation models that understand network behavior at a fundamental level. Unlike competitors who bolt on machine learning as an afterthought, our entire platform is built on AI-native principles, enabling true autonomous detection and response capabilities.
Cognitive Classification Pipelines
Automatic mapping to MITRE ATT&CK framework for comprehensive threat intelligence
Encrypted Traffic Analysis
LLM-based detection while preserving privacy and encryption integrity
Modern networks are heavily encrypted, making traditional deep packet inspection ineffective. Our LLM-powered analysis examines traffic metadata, behavioral patterns, and side-channel information to detect threats without breaking encryption.
This approach maintains privacy compliance while providing comprehensive threat detection across TLS 1.3, QUIC, and other encrypted protocols. Our models learn to recognize malicious patterns in timing, packet sizes, and flow characteristics that human analysts would miss.

Sensor Technology
Cyber Ninja's sensors are designed from the ground up for ultra-low-latency, high-throughput environments. Battle tested in production networks where latency and scalability matter most.

Designed for Speed
Built for speed and scale using Rust, our sensors deliver industry-leading performance with memory safety and zero-cost abstractions. Optimized for high-throughput environments from 1G to 100G+.
Cloud, Virtual or On-Prem
Zero-conf deployment. Support for major public clouds, private clouds and leading hypervisors. Deploy anywhere your network exists.
AI-at-Edge Detection
Generate detections on the sensor whenever GPU infrastructure is available. Reduces MTTD and ensures an added layer of protection with edge-based inference.
Industry Leading Network Throughput
Best-in-class DPI transport layer with optimized RSS for >100G throughput per sensor. Scales horizontally to handle the largest enterprise networks.
Tokenized Traffic Intelligence
Our sensors perform intelligent metadata preprocessing, transforming raw traffic into vectorized data. Using efficient filtering techniques, we extract, normalize, and enrich metadata from protocols and applications, surfacing only high-signal information for analysis.
Forensic Capabilities: Targeted PCAP Caching
Instead of dumping endless traffic logs, our system captures only what's relevant—driven by AI inference. Selected traffic is cached intelligently without the storage burden of full-time capture.